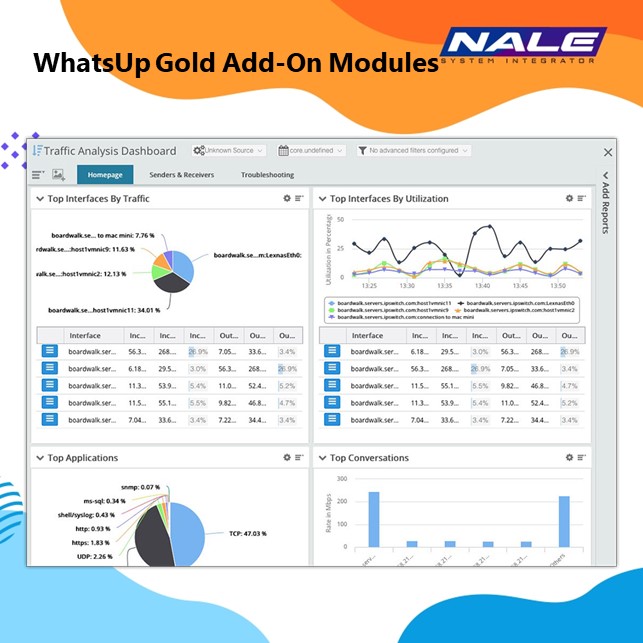
Network Traffic Analysis 25 Service Agreement with up to 1 Year Service
- Get detailed visibility to network traffic information on:
- Senders, receivers, and conversations
- Sender and receiver domains
- Sender and receiver countries
- Applications and protocols
- Incoming and outgoing interface traffic
- Incoming and outgoing interface utilization
- Bandwidth usage by host and group
Deskripsi
[vc_row][vc_column][woodmart_title align=”left” tag=”h2″ woodmart_css_id=”60a5cfcadd329″ title=”Deskripsi Network Traffic Analysis 25 Service Agreement with up to 1 Year Service” woodmart_empty_space=”” title_width=”100″][vc_column_text text_larger=”no”]Our Network Traffic Analysis module delivers detailed and actionable data on network traffic and bandwidth consumption, which helps you establish and enforce bandwidth usage policies, control ISP costs, secure the network, and provide the network capacity required by users, applications, and the business. It not only highlights the overall utilization of the LAN, WAN, and the internet, but also indicates which users, applications, and protocols are consuming bandwidth.
5 Superpowers You Get From Network Traffic Monitoring
- Network Traffic X-Ray Vision
Analyze netflow data to see things that just aren’t possible with SNMP like a port level analysis of applications consuming bandwidth, end-points (‘talkers’) consuming bandwidth by port and bandwidth consumption by end-point or application over time - Bandwidth Usage Super Intelligence
A utomatically track WAN usage by application for a month and then show management just what those monthly costs are paying for. Management likes IT pros that think about the business and you have all the factoids at your fingertips. - Network Omni-Presence
Some of your peers maybe worried that you are watching everything when they see reports that show who is using valuable bandwidth for games or videos when they should be working. But you’ll be on top of unauthorized activity that impacts end-user response times. - Super Network Optimization Skills
How about validating that your best laid QoS plans are actually working. Traffic monitoring at the network flow level can show you the affect of application prioritization schemes. - Cyber-Attack Antennae
Set alerts for suspicious conditions like spikes in failed connection attempts on a device. Quickly spot that all of the transmissions originate form a few IP addresses outside your network and you can block an external portscan before the attacker is successful.
[/vc_column_text][vc_column_text text_larger=”no”]Karena padatnya alur keluar-masuk barang, para pembeli wajib :
KONFIRMASI ketersediaan stok barang terlebih dahulu sebelum membeli.
CHAT kami untuk update stok maupun kebutuhan URGENT.
MELAYANI penjualan online maupun offline.
JIKA membutuhkan Konfigurasi & Implementasi, silahkan konfirmasi. (Maksimal 30 hari Setelah Pembelian)
Chat pada hari kerja : Senin – Jumat | jam 08.30 – 16.00
PT Nale System Integrator
Penyedia layanan IT TERBAIK dan TERLENGKAP di kota anda.
Didukung team profesional bersertifikasi dan berdedikasi.
Dipercaya oleh berbagai Corporate dan Institusi.
TERIMA KASIH[/vc_column_text][/vc_column][/vc_row]